Told You So -- ErrorSafe Pop-Ups Served via Ruckus
Thursday, August 16, 2007
Well, listening to my morning dose of Sara Groves, I saw a familiar pop-up that I'd called coming a short while ago (look towards the end):
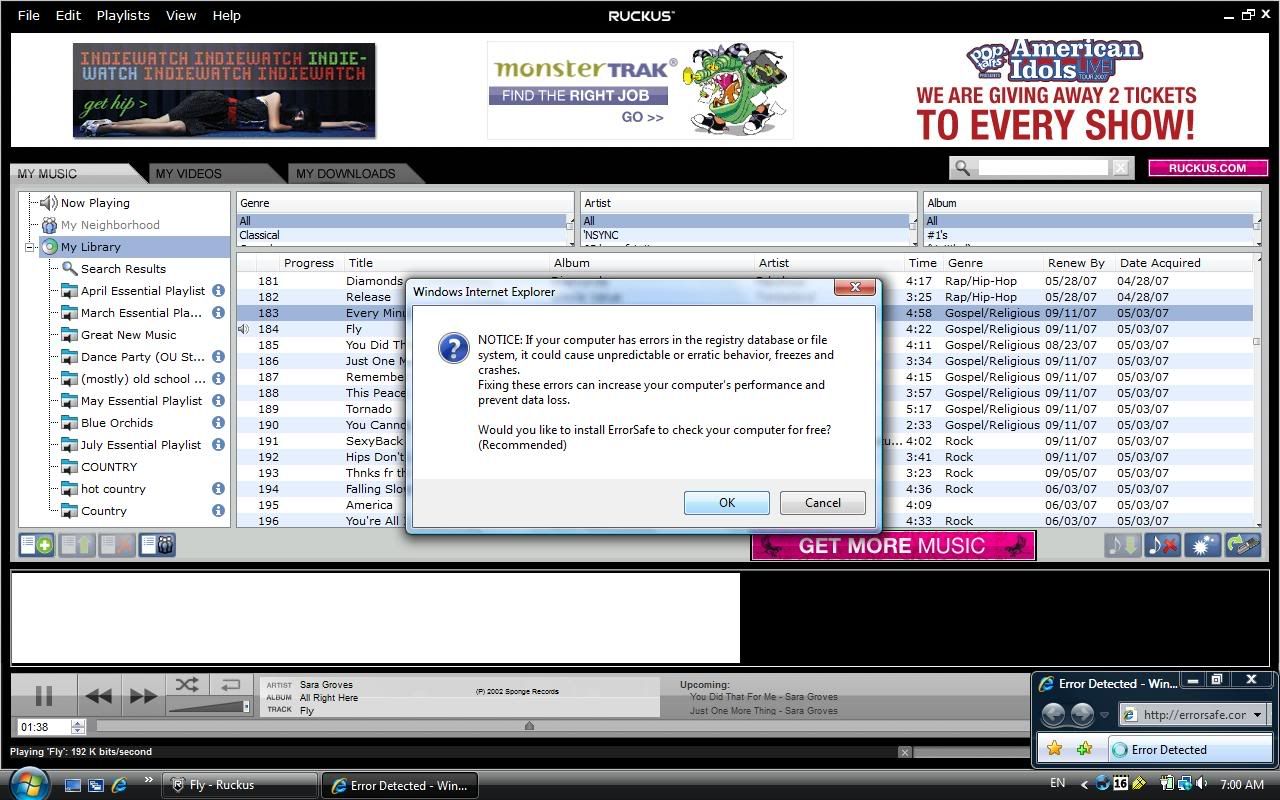
That's right, ErrorSafe! (If you're not familiar with the rogue AV/registry cleaner/etc. scene, such programs claim that there are a bunch of problems that need to be fixed...for a fee. They install without user consent, and have little or no real functionality). Clicking anywhere on the message (NOTE: even on the red "X" in the corner) loads the ErrorSafe install page in IE7:
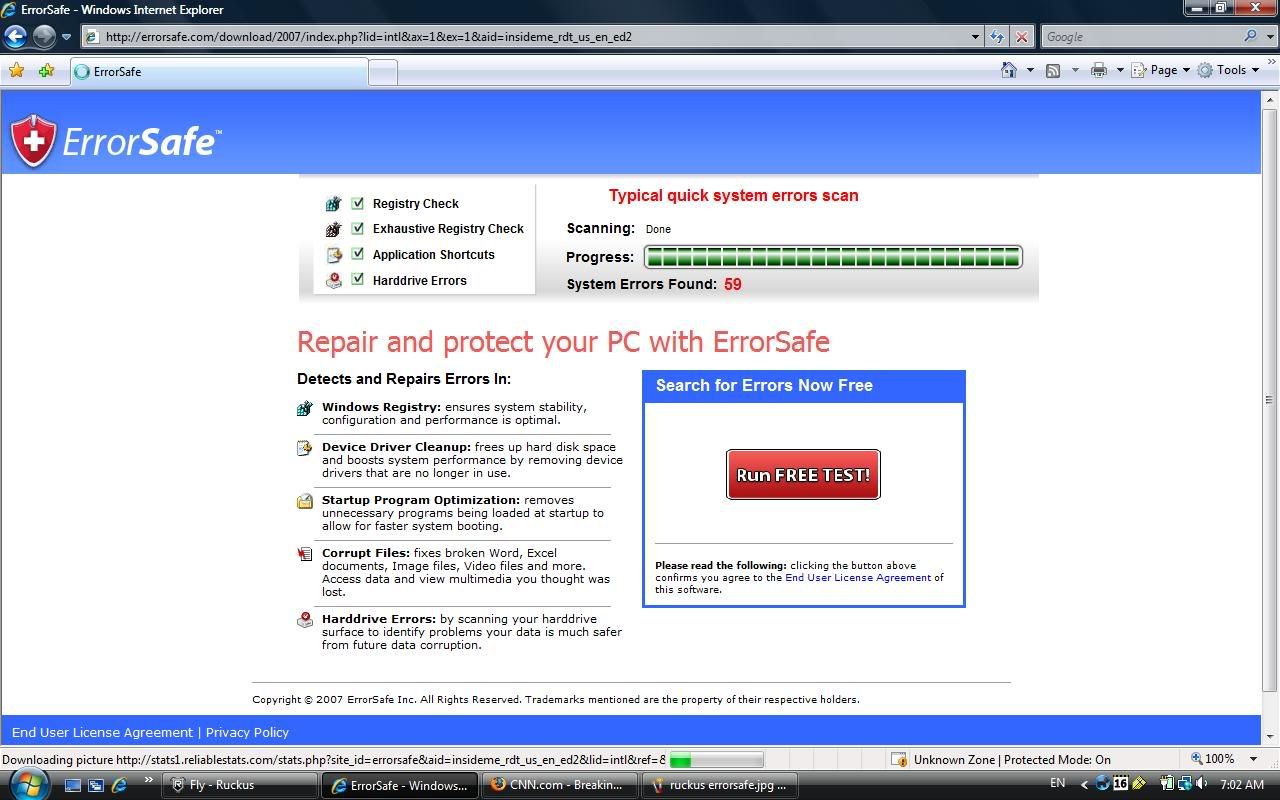
...and not only that, the page then attempts to install the rogue program without user consent (in this case, Symantec caught the .cab file while it was still in the Temporary Internet Files):
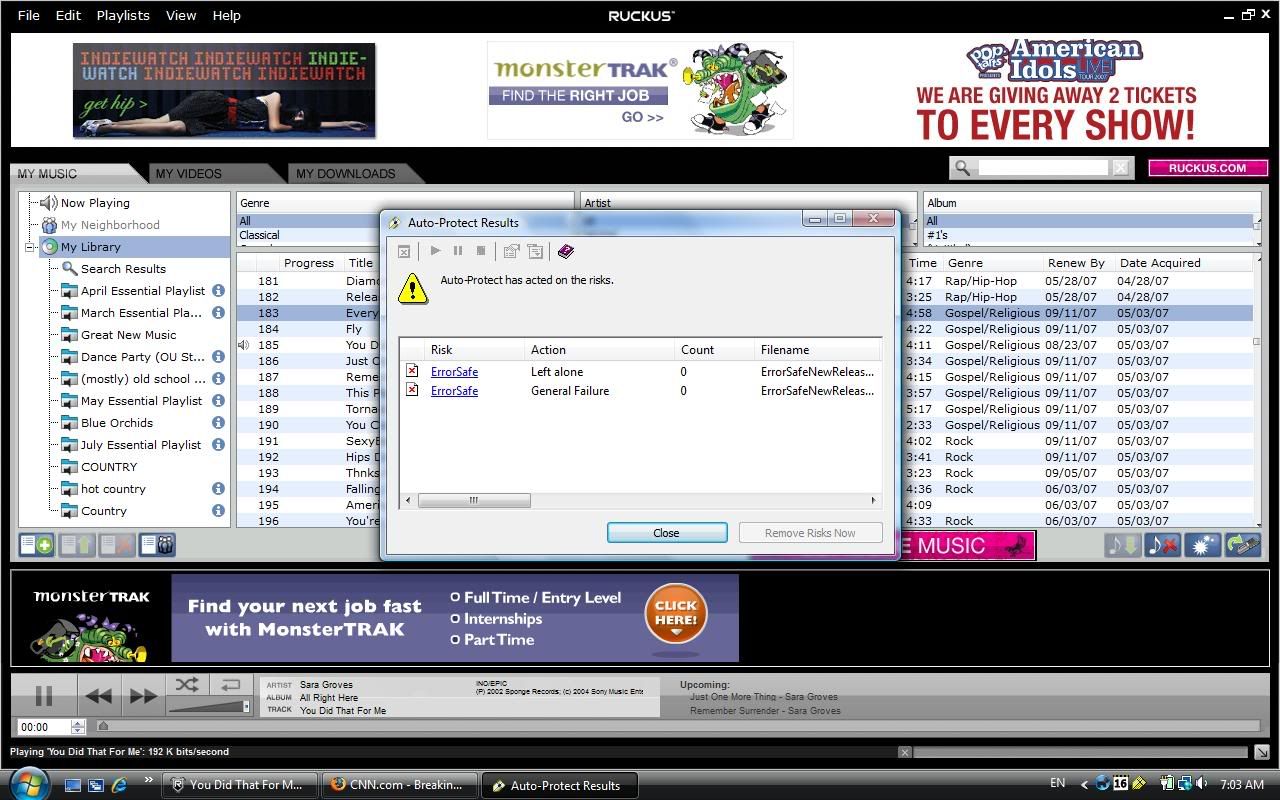
I've notified Ruckus about the advertisement, but it goes to show you the perils of 3rd-party ad networks. If you don't stay on top of the ads you're serving (or someone is serving on your behalf), something like this is bound to happen.
- David Oxley
UPDATE (8/17/07): Got hit with another redirect to errorsafe.com on Ruckus today, with two chief differences:
1) The product advertised was WinAntiVirus2007
2) The ad was Flash-based, and automatically opened the ErrorSafe page without any user interaction whatsoever.
Ugh. Ctl-Alt-Del, end-task iexplore.exe, and send Ruckus an e-mail (I've yet to hear back concerning my first experience...)
UPDATE #2 (8/17/07): Received a response from Ruckus saying that it's been cleaned. Likewise, see the comments for an apology from their senior director. I commend them on getting this taken care-of so quickly -- I'm not giving up my Ruckus anytime yet. :)
Labels: ads, errorsafe, ruckus, winfixer
posted by David @ 4:18 AM,
,
![]()
Ruckus Ads Get a Bit Too Much...
Sunday, August 05, 2007
First off, I love Ruckus. It's a free service that allows college students to download and listen to unlimited song tracks. The catch? All files are DRM-protected, time-limited (but are instantly renewed), and you have to suffer-through a single banner ad in the player. Big deal.
As we all know, though, banner ads can have their own issues. In the past, I have seen Ruckus ads try to run JavaScript, open new windows without user interaction, and run shady "You've Won -" offers. Ho-hum.
So what's new? Zango content. In particular, a steamy banner advertising:
"Anna Nicole Smith Lesbian Bathtub Sex Part I"
...classy. This is a new one to my knowledge -- porn offered by Ruckus ads?
The yieldmanager ad redirects to zango.com where, not surprisingly, the user is presented with thumbnails of several supposed porn movies featuring the late Anna Nicole Smith, with the caveat that an install of Zango's adware is in order. Being rather opposed to the stuff myself (both Zango and porn, that is), I let the ad recycle. H&R Block. That's respectable.
Needless to say, care is in order. I wouldn't be surprised to see a rogue AV scanner in there sooner than later, and sneaking IFRAMEs and exploits has been done with shady affiliate networks in the past...
- Nexus7
posted by David @ 1:47 PM,
,
![]()
A Little Phish-Finding
Wednesday, August 01, 2007
Well, I was bored. So what does an InfoSec student do when he's bored?
Hunt phishers, of course.
First, I headed over to SiteAdvisor to try and find an active phishing site. A Wells Fargo site is being hosted on a hacked immigration-support site:
hxxp://www.americanimmigrationnetwork.com/AAAA%20Kits/incudes/www.wellsfargo.com/wellsfargo/Updates_info/
Nothing special, mind you, just your standard hacking package. After a bit of fun with the source code and Tamper Data, I found the mailer, update.php. Unfortunately, all e-mailing is handled server-side (duh), so I had to try and find the uploaded PHP file. This was made *quite* easy by the hacker(s) leaving the entire uploaded kit, includes.zip, behind. Doh.
Upon extracting update.php, I found the following interesting bits:
1) A given author of "KELVINROLEX" Googling the name returns a Mobango account for a Nigerian man with the same handle. (NOTE: I am NOT saying that this is the same guy! There is no evidence of that whatsoever, save for what we know of Nigeria and scams...)
However, there *is* another link that I think is safe to assume our phisher is responsible for. Meet the "Kelvinrolex Php Mailer," a lame attempt at God-knows-what. It calls itself a "Spamer Inbox," but it seems to have no real functionality (and at version 1.5, no less). Whatever. Kelvin's phishing script isn't all that much more interesting...the guys uses Frontpage, for chrissake!
2) An e-mail addy: dv_max4009@yahoo.com
This little gem returns several hits on Google. Meet David Alvin Maxwell, a nice gent who spends his time defrauding women with romance scams. I guess the photos of legit models isn't all he's stealing these days...
3) A second e-mail address: lurdofhonor@gmail.com
No hits on Google, unfortunately.
Interesting part? Though Mr. Mobango is innocent until proven guilty, Mr. Maxwell is also from Nigeria. Hmmm.
Gotta love those anonymous Internets, waiting to be pillaged and plundered by techno-pirates such as KELVINROLEX and dv_max4009. Erm, Kelvin and David. From Nigeria. *grin*
- Nexus7
Labels: phishing
posted by David @ 6:57 PM,
,
![]()
